Today’s advanced technology users are demanding single login capabilities, also known as single sign-on (SSO), to access multiple applications throughout the customer landscape. To achieve this, most leading cloud applications such as SAP C/4HANA, SAP S/4HANA, SAP CPI (Cloud Platform Integration), and SAP CPQ (Configure Price & Quote) store user credentials on the cloud portal.
Customers and users prefer to use their existing user stores to easily access all their critical applications. Is it safe to say that the SSO concept is beneficial to users? That’s a big YES. SSO serves the purpose of remembering the user login credentials for various applications. By setting up SSO in this manner among applications and user stores, it is possible to use a single password for all applications configured in the system. What’s more, this also helps clients to reduce the accumulation of service tickets for password reset at the helpdesk.
The User Credential Stores Authentication Method
- SAP IDP (Identity provider): This is one of the most popular user stores used to setup SSO with multiple SAP applications
- MS-ADFS (Active Directory Federation Service): This is Microsoft’s application wherein user details are stored. ADFS is used to store or activate/enable the unique user-ID and email ID, which is, in turn, used to connect the other applications via SSO
- Azure Active Directory: It provides SSO and multi-factor authentication to protect users from cybersecurity attacks
- Okta: This is another Active Directory option when it comes to enabling SSO
It is often possible that existing user stores (Active Directory) are available with the client. In such scenarios, the businesses can leverage them to set up SSO for different applications. Our team has managed various scenarios to set up multiple SSOs with different user stores for different applications.
Here are a few of the examples worth sharing.
1. SAP C/4HANA SSO setup with SAP IDP:
This kind of scenario is useful whenever the client wants SSO set up with more than one application. For this particular customer, we set up SSO between SAP C/4HANA, SAP CPQ, and SAP IDP. In the case of our customer, we set it up in such a way that, while logged into SAP C/4HANA, the client could use the SSO URL of SAP C/4HANA and employ the user credentials defined in SAP IDP to log into the SAP C/4HANA platform. This SSO URL can be edited as and when needed; however, I would advise you to retain the default SSO URL as-is.
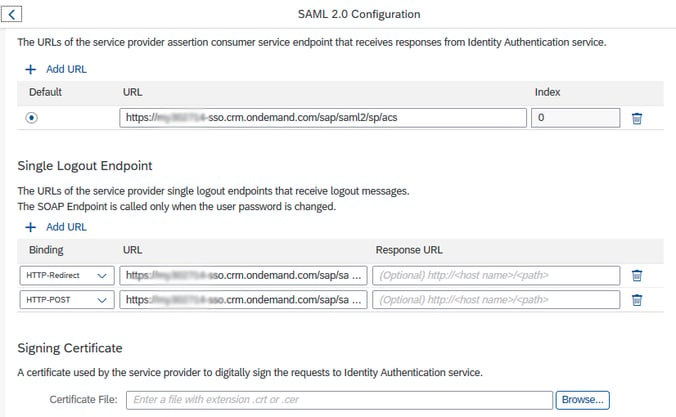
By clicking on the browse button (as shown in the above image), we can upload the metadata file of the Identity Provider.
This SSO URL will be automatically set up once we upload the SAP C/4HANA metadata file into SAP IDP.
At the same time, we have to pull the metadata file from SAP IDP and upload it into SAP C/4HANA for handshake.
This mapping can be done based on certain attributes; for instance, the USER name in SAP C/4HANA should be the same as the Login Name in SAP IDP.
As mentioned earlier, to enable SSO with more than one application, we can create a mashup in SAP C/4HANA for SAP CPQ and share the metadata file of CPQ with SAP IDP to establish a handshake.
This SSO scenario was most recently enabled for a leading North American manufacturer of engineered wood products.
Similarly, we implemented a similar scenario for SAP C/4HANA and SAP Portal using SAP IDP by creating a mashup for the SAP portal application in SAP C/4HANA.
This SSO scenario was most recently enabled for a leading express parcel service provider.
2. SAP C/4HANA Setup with ADFS:
If the client has ADFS as the existing user store data, it is possible to use the same user store to set up SSO for SAP C/4HANA. Now, this is one of the critical scenarios wherein the user has already logged in on his laptop using ADFS credentials (i.e. using the user/password combo). He then has to just click on the SAP C/4HANA SSO URL, and it will be redirected to the SAP C/4HANA application without prompting a login screen.
This requires the combined efforts of the ADFS admin (who performs the configuration from the ADFS side) and the BASIS admin (who does the configuration on the SAP C/4HANA side).
To enable this configuration, we would need to follow certain thumb rules; for instance, care has to be taken to ensure that the SHA (secure hash algorithm) needs to be the same as the algorithm being used in the SAP C/4HANA and ADFS end (i.e. either the SHA-256 or the SHA-1 algorithm).
This SSO scenario was most recently implemented for two of our clients: a leading global appliance company and a leading producer and distributor of premium specialty alloys.
3. SAP C/4HANA SSO Setup with Azure AD and SAP Portal Application:
This scenario is quite similar to the above mentioned ADFS SSO setup. The only difference in this case is that we are considering more than one application i.e. SAP Portal application for SSO setup using Azure AD in addition to SAP C/4HANA. That makes it a collaboration between three applications in all.
This SSO scenario was most recently implemented for two of our clients: a veteran web company and a world-class leader in design, manufacturing, and marketing of power tools.
4. SAP C/4HANA SSO Setup with Okta User Store:
For this customer, the popular cloud-based user store, Okta, was used for setting up SSO with SAP C/4HANA. I’d like to mention here that this SSO setup process is the most user-friendly when compared to all the above mentioned options.
This method simply involves adding the new application tab by leveraging the admin rights in Okta and sharing the metadata file for handshake.
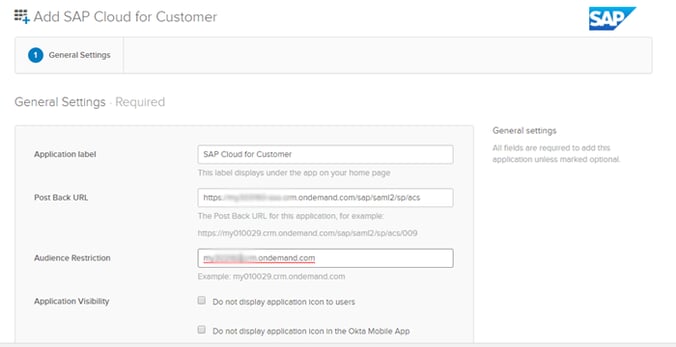
This SSO scenario was most recently enabled for two of our customers: a leading manufacturer and supplier of engineered flow components and a leading provider of workforce management cloud solutions.
5. SSO Setup Client AD User Store with SAP S/4HANA-Default SAP IDP:
These days, cloud applications such as SAP S/4HANA Cloud are by default a part of the SAP IDP user store. This means that the SAP S/4HANA Cloud user credentials are maintained by default in SAP IDP. But then, some clients insist on using the existing user store, i.e. Azure AD or ADFS instead of the default SAP IDP.
This means that we have to setup the SSO in the existing default IDP. In this scenario, SAP IDP was set up as the proxy and Azure AD/ADFS was used as the primary user store.
We recently enabled this SSO scenario for a computer software brand that specializes in a cloud-based mobile data collection platform.
Bringing more insights and suggestions to you throughout 2020
Our team has grown in 2019, and we have more exciting projects and fun updates that we would love to share with you all. If you found this blog useful, make sure you are among the first to see our updates in 2020. Subscribe today to Knack Systems to receive future alerts in your inbox!

